COMP3052 Computer Security 3 -- Authentication
Lecture 4 Authentication
Authentication ensures:
- Someone are permitted to access the asset
- Someone are who they say they are
understandCredentials:
- Something they are
- Something they have
- Something they know
Username & Password
- First step: identification - you announce who you are
- Second step: authentication - you prove that you are who you claim to be.
- Time of check to time of use (TOCTTOU) 这是一个软件设计上的竞争条件
- 解决方法:The operating system checks a user's identity at the start of a session but uses the identity to make access control decisions later on during the session
Password
Problems with passwords:
- Forget
- Guess
- Spoofing and phishing
- Comprimised password files
- Keylogging
- Weak password
[UNDERSTAND] Password Policies
- Certain length, certain types of characters / No dictionary words / Change regularly / No previously used passwords
Storing passwords
- Use a one-way hash function
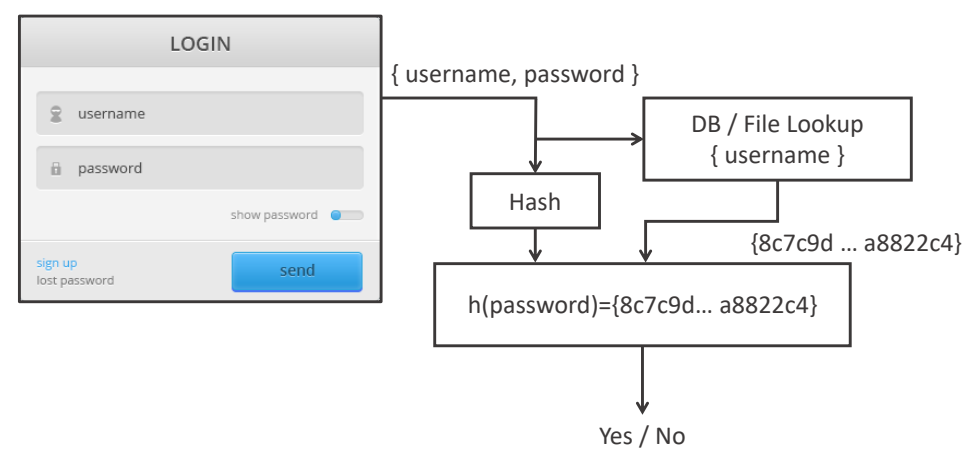 Password / Shadow Files that stored
passwords are read protected
Password / Shadow Files that stored
passwords are read protected
Cracking Passwords
- Offline: you have a copy of the password hash locally
- try lots of possible passwords and see if we have a hash collision
with a password list
- brute force
- dictionary attack
- try lots of possible passwords and see if we have a hash collision
with a password list
- Online: you do not have the hash, and are instead attempting to gain
access to an actual login terminal
- usually attempted with phishing
[UNDERSTAND] Password Salting (improve security)
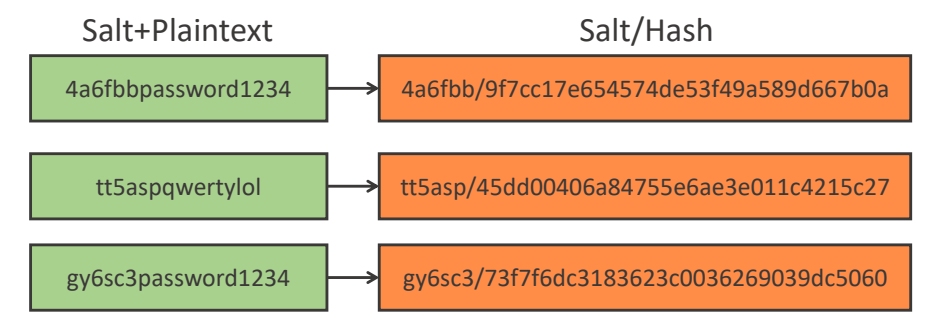
- Cracking multiple passwords is slower - a hit is for a single user
- Prevents rainbow table attacks (reverse hash directly)
- But salting has no effect on the speed of cracking a single password.
Multi-Factor Authentication
- Password are something you know
- MFA conbines something you know with something you
have
- Text code to mobile
- Google/Microsoft Authenticator
- One time password
- USB devices
Biometrics
Combine something you know with something you are
- Fingerprint
- Retina recognition
- Voice...
Accuracy of a biometric system is important:
- FP rate
- FN rate
COMP3052 Computer Security 3 -- Authentication
https://jerry20000730.github.io/wiki/Lecture Note/COMP3052 Computer Security/CS5/
